Cyber Program Operations
As we embrace the digital-first revolution, cybersecurity has become more of a necessity than an added advantage. Innovative and futuristic organizations positioned for growth need to place cybersecurity at the core of their business transformation strategy to ensure safe and secure functioning. Explore our comprehensive suite of cyber solutions that are tailored to envision, enable, and enhance security!
Our Services
-
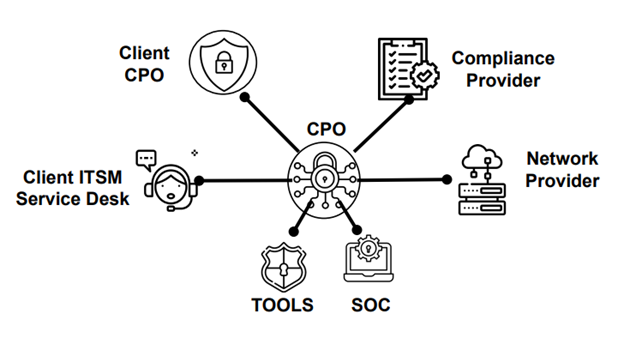
Cyber Program Operations (CPO)
- Handle NIST governance and compliance for cybersecurity (GV and ID)
- Define, design, and manage the cyber program
- Conduct risk assessment and mitigation
- Design a data protection and attack surface management framework
- Increase organizational resilience through training and cultural awareness
-
Security Operations (SOC)
- Initiate cyber tool configuration and management
- Institutionalize threat intelligence and vulnerability assessment
- Enhance the incident identification response time
- Devise a forensics and recovery framework
-
Security Tooling (TOOL)
- Deploy foolproof vulnerability and risk identification
- Robust identity, data, network, and E-mail protection
Key Benefits of our Unique Offshore CPO Approach
- Broader Scope of Cybersecurity Risk Management
- State-of-the-art process and documentation maturity
- Sustainable solutions to mitigate single point-of-failure risks
- Value-driven cost efficiency and optimization
- Continuous and scalable improvement of the cyber stack
Contemplating your next big move in the cybersecurity domain? Connect with our experts today for a detailed know-how of our cutting-edge solutions!
Contact Us